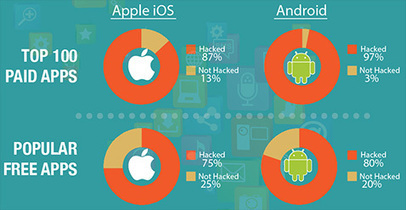
A study of 40 mobile commerce apps shows hackers are posting copies of retailers’ apps to secondary app stores, copies designed to capture and transmit confidential customer information that can be used to commit fraud.
90% of Android retail mobile apps and 35% of Apple iOS retail mobile apps have been duplicated and published to secondary app stores by hackers seeking to disrupt retailers’ mobile activities or collect confidential customer information that can be used to make fraudulent transactions, according to the Third Annual State of Mobile App Security report from Arxan, a web and mobile security technology firm. A secondary app store is any app store other than Google Play, the primary Android app store, and the Apple App Store, the primary Apple iOS app store.
Learn more:



 Your new post is loading...
Your new post is loading...






A study of 40 mobile commerce apps shows hackers are posting copies of retailers’ apps to secondary app stores, copies designed to capture and transmit confidential customer information that can be used to commit fraud.
90% of Android retail mobile apps and 35% of Apple iOS retail mobile apps have been duplicated and published to secondary app stores by hackers seeking to disrupt retailers’ mobile activities or collect confidential customer information that can be used to make fraudulent transactions, according to the Third Annual State of Mobile App Security report from Arxan, a web and mobile security technology firm. A secondary app store is any app store other than Google Play, the primary Android app store, and the Apple App Store, the primary Apple iOS app store.
Learn more:
- https://gustmees.wordpress.com/2014/03/05/often-asked-questions-are-there-cyber-security-dangers-with-apps-and-whats-about-privacy/