The need to outperform competitors makes it imperative for manufacturing organizations to protect their intellectual property. Manufacturers need to raise the bar when it comes to security and in order to reap the benefits of Industry 4.0, leaders must support IT teams to help them secure networks.
Via JC Gaillard, massimo facchinetti



 Your new post is loading...
Your new post is loading...



![Protecting Your Password - How Hacker Friendly is Yours [Infographic] | Information Technology & Social Media News | Scoop.it](https://img.scoop.it/_2G3yRb429iCkAsLUS3C0Dl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)


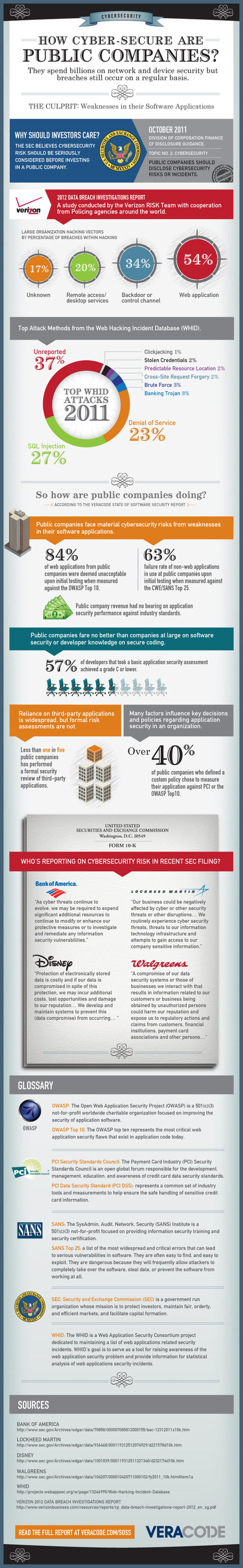
![Increase of Web Attacks 2010-2012 | mLearning - BYOD [Infographic] | Information Technology & Social Media News | Scoop.it](https://img.scoop.it/-tguB3uphVbs_59FcwUZjzl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)

![7 Cybersecurity Myths Busted [Infographic] | Information Technology & Social Media News | Scoop.it](https://img.scoop.it/B-jkKo7ABgUaxD2BjEN8YDl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)

![Are you a hacker's target? [infographic] | Information Technology & Social Media News | Scoop.it](https://img.scoop.it/rt5wG9S2kMN-82Pg7fPKsDl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)